Tears of the Phucked.
Phuctor - rewritten and revved up on new hardware in April - is presently eating SSH RSA keys from a scan of the complete IPv4 space.
And, on occasion, breaking some.
And generating other laughs as well. In today's server logs:
134.223.116.158 - - [22/Jul/2016:15:54:57 +0000] "GET /gpgkey/50840391E5677882196999C9AE77F3177E6CBF8D35FB4F1FEF848CFADF9088B1 HTTP/1.1" 200 3425 "http://134.223.116.149:15871/cgi-bin/blockpage.cgi?ws-session=2010817170 "
What's that? A 'Websense' censortron control panel, apparently.
Who might it belong to ? Could it be:
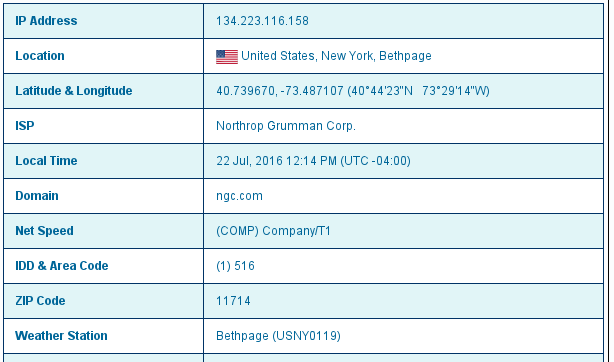
Isn't it just a little bit too late for this nonsense? Plus, your monkemployees can still read the page when they clock out and go home. Or on their phones, in the toilets, etc. Why bother with this nonsense ? Phuctor isn't even a 'wikileak' or the like, it is merely one of the public whipping posts to which you have been tied, by your own hands, long ago.



